What do I mean by a “full-bore CISO?” For the larger firms, I mean a heavily credentialed and experienced data security expert, the type who comes with a 6- or 7-figure price tag, and whose background is from the likes of the NSA or companies in comparably sophisticated leagues. (I didn’t say this would be cheap, but neither is dissolution as a going concern.)
And another thing: Whatever your CISO recommends needs to have the same force as if it came from the Managing Partner and Executive Committee. No worming around it or taking an appeal.
I have another theory—the even less flattering one—about why Law Land is vulnerable: Partners who think they know better and are too smart or can’t be bothered. I can, without meeting any of the offenders lurking within your firm, assure you with a high degree of confidence of their response were you to challenge them on their security hygiene: They would lecture you with certitude and an air of finality that they know better and that nothing could possibly go wrong.
Secretaries, paralegals, and most of your partners and associates wouldn’t do that. Only the Super Egos will. But as usual, that’s who you need to watch out for.
I have zero knowledge of what might or might not have happened at Cravath and Wachtell, and the point of this article is that we all need to belatedly start to take this stuff with dead seriousness, but I can’t help but point out that my ego-driven exceptionalism theory is fully consistent with the most elite firms being vulnerable—they house the most super-sized egos.
It’s been said that the biggest “or” in the English language is the one in this phrase: “knew or should have known…”
By that standard, you have no further excuses.
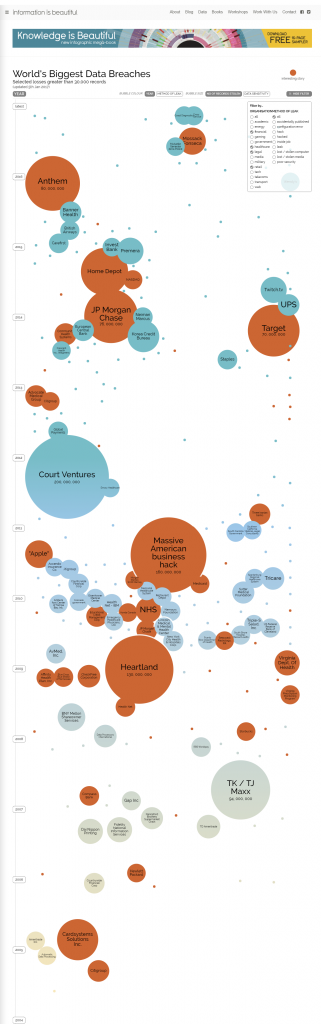
Regular readers know that I’m fond of data, so here’s some.
Courtesy of the ingenious “Information is Beautiful” site, here is a diagram of:
- Every known data breach since 2004
- Involving at least 30,000 records
- In the financial services, healthcare, legal, and tech sectors
- Resulting from hacking or an inside job/leak.
The size of the bubbles corresponds to the number of records stolen and, for present purposes, you can ignore the blue and orange colors. (Orange represents what the “Information is Beautiful” folks think is a particularly interesting story.)
Don’t say you couldn’t see it coming.



In the natural-resource industries, there is great prestige associated with what is known as “wealth generation.” But there are a variety of hazards that can put initially-generated wealth at risk, in extreme cases can obliterate it and leave residual liabilities. One of approaches to management of such risks is to have a “downstream” function for “wealth preservation;” a CISO (and her/his team) would fall into this category. What should not be surprising is that the downstream functions such as information security typically do not carry the prestige of the upstream functions. As Bruce’s entry indicates – “wealth preservation” must have an established role that ensures that its responsibilities are executed by the corporation/partnership. Surely, the shareholders, if you asked them, would agree.
Mark:
Thanks as always for your insights; a theme of Adam Smith, Esq. is that Law Land has much to learn from industries in the other 98% of the economy and this is a grand example.
You and other readers will see, however, in my forthcoming book Tomorrowland that the partnership model of organization, as implemented by the vast majority of law firms, stands astride the road to such sane firm hygiene as you propose, blocking the way. How so?
It severs any conventional tie between the interests of the the individual partners and the firm’s long-term health; partners are the ultimate self-contained portable assets. I imagine the only exception would be if Firm X failed because of such a spectacularly flagrant cyber-breach that individuals associated with it were tarred reputationally. But when potential lateral partner revenue is on offer, I fear memories are short.
In any event, you will see in the forthcoming book why I recommend that all but the most elite handful of firms abandon the partnership structure.
Thanks again.